| Rating: 4 | Downloads: 5,000,000+ |
| Category: Tools | Offer by: Authy |
Authy is a popular mobile application that aims to enhance online security by simplifying the process of two-factor authentication (2FA). With its user-friendly interface and robust features, Authy provides a convenient and secure way for users to protect their online accounts. This article explores the various features and benefits of the Authy App, examines its pros and cons, includes user reviews, and suggests similar apps for those seeking alternative options.
Features & Benefits
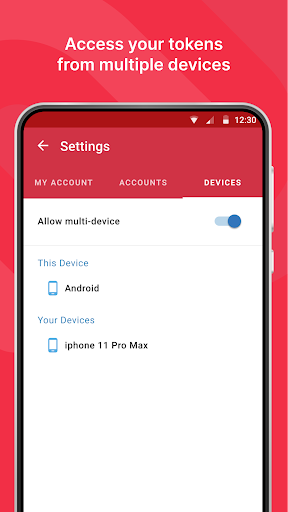
- Multi-Device Syncing:Authy allows users to sync their accounts across multiple devices, providing seamless access to their 2FA codes. This feature is particularly beneficial for those who use multiple devices or need to switch to a new device without the hassle of reconfiguring their accounts.
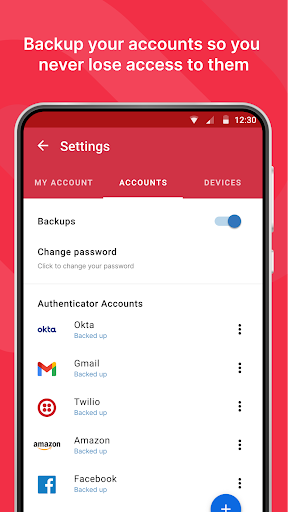
- Backup and Recovery:Authy offers a secure backup and recovery system, ensuring that users do not lose access to their 2FA codes. In the event of a lost or stolen device, users can easily restore their accounts on a new device using their Authy credentials, eliminating the risk of being locked out of their accounts.
- One-Tap Authentication:Authy simplifies the authentication process by allowing users to generate 2FA codes with a single tap. This eliminates the need to manually enter codes, saving time and reducing the likelihood of errors. The one-tap authentication feature enhances convenience while maintaining a high level of security.
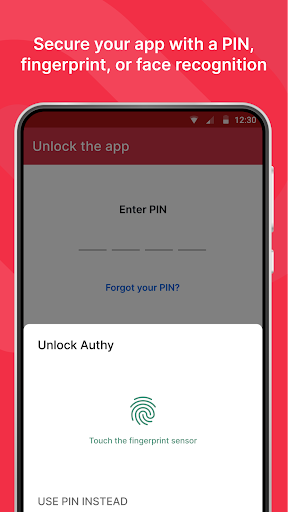
- Secure Cloud Encryption:Authy employs strong encryption protocols to securely store user data in the cloud. This ensures that users’ sensitive information, including their 2FA codes, remains protected from unauthorized access. Authy prioritizes user privacy and implements robust security measures to safeguard user accounts.
- Multi-Account Support:Authy supports a wide range of online services and platforms, allowing users to store 2FA codes for multiple accounts in a single app. This centralized approach simplifies the management of 2FA codes and reduces the need for multiple authentication apps.
Pros
- Convenient Multi-Device Sync: Authy’s ability to sync 2FA tokens across multiple devices ensures seamless access to accounts without the hassle of reconfiguring settings. This is particularly beneficial for users who regularly switch between devices or have multiple devices.
- Backup and Restore Functionality: The backup and restore feature in Authy provides peace of mind, as users can easily recover their 2FA tokens in case of device loss or upgrade. This eliminates the risk of being locked out of accounts and simplifies the process of transitioning to new devices.
- Secure Cloud Storage: Authy’s use of secure cloud storage ensures that users’ 2FA tokens are protected from loss or theft. Storing encrypted tokens in the cloud adds an extra layer of security and provides a reliable backup in case of device failure.
- User-Friendly One-Touch Approval: Authy’s one-touch approval feature streamlines the 2FA process, making it quick and convenient for users. With a simple tap on their mobile devices, users can approve login requests without the need to manually enter codes.
- Centralized Multi-Account Support: Authy’s support for multiple accounts within a single app simplifies the management of 2FA for users with multiple online services. Having all 2FA tokens in one place eliminates the need to juggle multiple apps, providing a centralized and efficient solution.
Cons
- Dependency on Internet Connectivity: Authy requires an internet connection to function properly. In situations where there is limited or no internet access, users may face difficulties in accessing their 2FA tokens and approving login requests.
- Single Point of Failure: Since Authy stores 2FA tokens in the cloud, there is a single point of failure. If the cloud storage experiences a security breach, it could potentially expose users’ tokens. However, Authy employs robust security measures to mitigate this risk.
- Limited Integration Options: While Authy supports a wide range of platforms and services, there may be certain online services that do not offer compatibility with Authy’s 2FA solution. In such cases, users may need to resort to alternative 2FA methods or apps.
- Potential for Device Loss: If users lose access to their Authy app and do not have a backup or recovery method in place, they may face difficulties in regaining access to their 2FA tokens. It is crucial for users to set up backup options to prevent this scenario.
- Dependency on App Support: The availability of 2FA support for online services depends on the integration and support provided by those services. If a particular service does not support Authy’s 2FA solution, users may need to opt for alternative methods.
Apps Like Authy
Microsoft Authenticator:?Microsoft Authenticator provides secure 2FA for Microsoft accounts and other online services. It offers fingerprint and facial recognition for quick authentication.
Google Authenticator:?Google Authenticator is a widely used 2FA app that generates time-based one-time passwords (TOTP) for secure logins. It offers multi-device support and is compatible with various online services.
LastPass Authenticator:?LastPass Authenticator is a secure 2FA app that provides one-tap authentication and backup options.3.?Duo Mobile:?Duo Mobile offers two-factor authentication with features like push notifications and biometric authentication. It supports a wide range of platforms and services.
Screenshots
 |
 |
 |
 |
Conclusion
Authy is a user-friendly mobile app that simplifies the process of two-factor authentication. With its multi-device syncing, backup and recovery system, one-tap authentication, secure cloud encryption, and support for multiple accounts, Authy provides users with a convenient and secure solution for managing their 2FA codes. While there are some minor drawbacks, such as the initial setup process and occasional synchronization issues, Authy remains a reliable choice for individuals seeking to enhance their online security.


